Thanks for watching our CyRise demo day pitch!
With Scram, you can take control of your own data, securing it from unauthorized access. Thanks for attending our CyRise presentation.
Register for exclusive early access to our software!
Privacy notice: this form is exclusively used to get in touch with you via email following the CyRise Demo Day. We will reply to you personally. We won’t add you to a mailing list, we will always keep your details private. Here’s our privacy policy.
We think the system is very well planned and designed… My overall view is that the ScramFS system is a very solid cryptographic solution to the problem it intends to address. ScramFS is a system very carefully designed by a top cryptographer with highest professional standard.

Professor Jintai Ding, Ph.D. (Yale)Cryptographer and Professor of Mathematics, The University of Cincinnati
The security model allows for a very powerful attacker who can control all of the storage as well as the inputs to the ScramFS client. There are careful proofs that even this powerful attacker cannot read directory names or file contents, nor modify the data without detection.

Dr Vanessa Teague, Ph.D. (Stanford)Cryptographer and Senior Lecturer, The University of Melbourne
ScramFS’s Security Requirements span both confidentiality (“file system privacy”) and integrity (“file system integrity”). Scram’s ongoing demonstrated commitment to security is very encouraging for its future evolution.

Dr Toby Murray, D.Phil (Oxford)Software security expert and Lecturer, The University of Melbourne
Previous
Next
Here’s a technology recap!
ScramExplorer – end to end encryption for cloud storage
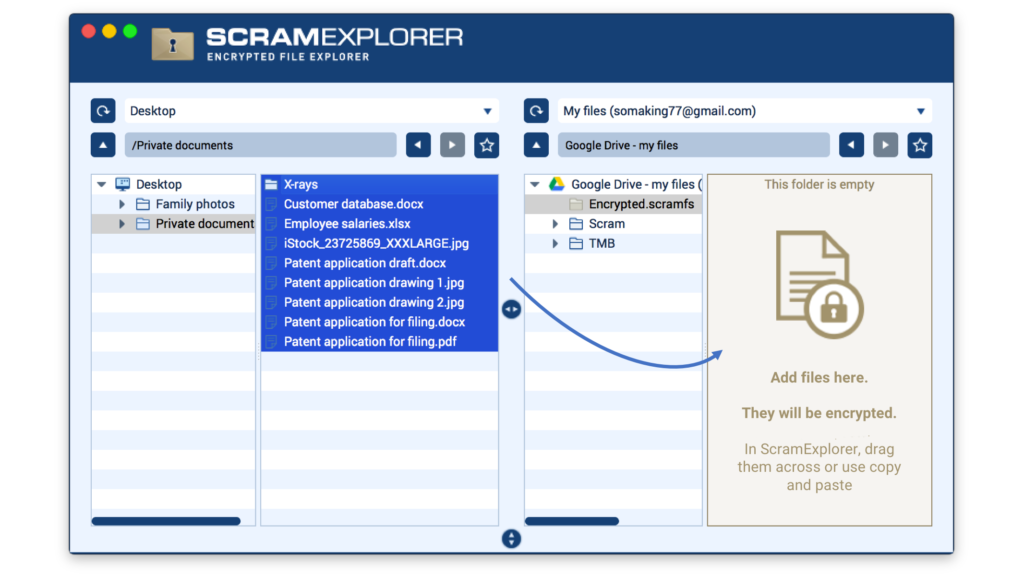
Need to secure your files in the cloud with end to end encryption?
With ScramExplorer, just create an encrypted directory on your favourite storage account, and everything will be copied there… encrypted!
This is great for high-security situations like investigations, and any time you need to keep your data safe from both 3rd parties and your cloud provider.
ScramNotes – secure notepad
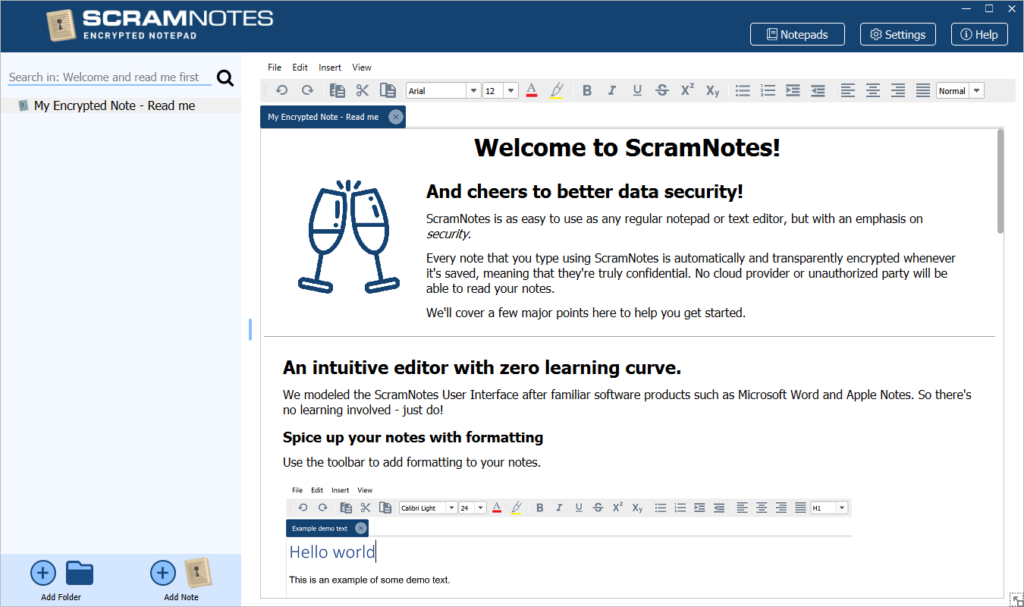
We all need to take notes and documentation – maybe they’re commercially sensitive and contain trade secrets. Other times they contain personal information.
ScramNotes guarantees the security of all your notes by encrypting them whenever they get saved to disk or to the cloud. The security is built-in, so you are always protected – it’s impossible to “forget” to encrypt the data, or to save it to the wrong location.
ScramGet – secure cloud-to-local backups
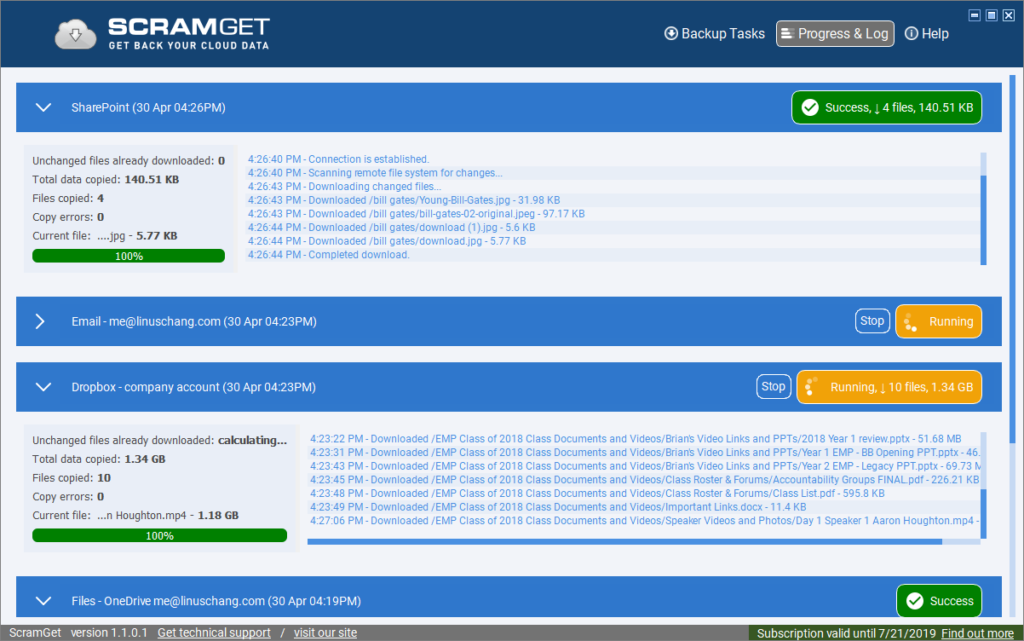
Is your only copy of data in the cloud?
More and more, we see problems like account hijacking or intentional data deletion. Business and people losing their data permanently. The VFEmail hack is a good example. Businesses often need to retain data for years or decades – sometimes for compliance, and sometimes for legal protection.
Cloud data needs backups and protection just like on-premise data. However, many people confuse deleted item retention with backup, only to discover when it’s too late.
ScramGet automatically backs up and protects cloud-data by downloading it on schedule. This is great for long-term backup and data retention.
All secured with ScramFS: our peer-reviewed, post-quantum safe cryptographic file system
The rigorous level of design and peer review is what distinguishes ScramFS from other crypto implementations.
If you care about or have studied cryptography, you probably know that most crypto is flawed because it was improperly designed and improperly implemented. Many open source implementations contain design and implementation flaws.
ScramFS is the world’s only cryptographic file system that has been professionally designed by one of the world’s leading cryptographers (Dr Ron Steinfeld, Monash University) and been subjected to multiple rigorous peer reviews by cryptographers and software security specialists.
ScramFS is built exclusively on the AES-256 block cipher, constructed to be post-quantum safe, and following the recommendations from the PQCrypto project. Technically, the following cryptographic and coding mechanisms are used in ScramFS.
- Authenticated encryption with associated data (AEAD) scheme: AES-256 block cipher used in the Galois counter mode as described in Morris J. Dworkin, “Recommendation for block cipher modes of operation: Galois/counter mode (GCM) and GMAC”, 2007. NIST special publication 800-38D.
- Deterministic authenticated encryption with associated data scheme: AES-256 block cipher used in the SIV authenticated encryption mode algorithm described in P. Rogaway and T. Shrimpton, “Deterministic Authenticated-Encryption”, 2007.
- Fixed input-length pseudorandom function: AES-256 block cipher with key length 256 bits and input length 128 bits generating a pseudorandom output of length 128 bits.
- Variable input-length pseudorandom function: Uses the authentication tag generated by the authenticated encryption (AEAD) scheme with the initialization vector set to the input and empty plaintext and associated data.
- Filename character encoding (non-cryptographic): choice of using a custom encoding known as Base32k, or standard Base64 or Base32.